Asus no longer updates the codebase for the software that ran my trusty RT-AC66U wifi router. So, what started out as a project to replace the router with an updated model has evolved into a complete revamp of my home network model. Criteria for the new network included the ability to segment and secure the network for home devices, guest wifi and Internet of Things (IoT) devices. I have met the criteria with Ubiquiti EdgeRouter X and UniFi.
I chose products from Ubiquiti Networks as the core of my revised home network based, in part, on a glowing recommendation by security researcher Steve Gibson at Gibson Research Corporation. There is a fantastic HOWTO written by Mike Potts that is available at his GitHub page here that I used as a reference document. Useful if you choose to design your network with Ubiquiti network products.
Fiber to my home is terminated at the Bell Home Hub 3000 (HH3000) which provides connectivity for Internet and Bell Fibe TV (refer to my updated post on the configuration of the Bell Home Hub 3000 here). All wifi is disabled on the HH3000 except of the hidden 5GHz wifi network that is required for Fibe TV. The Ubiquiti products used in the new design are EdgeRouter X, UniFi AP AC LR Access Point and UniFi Mesh AP.
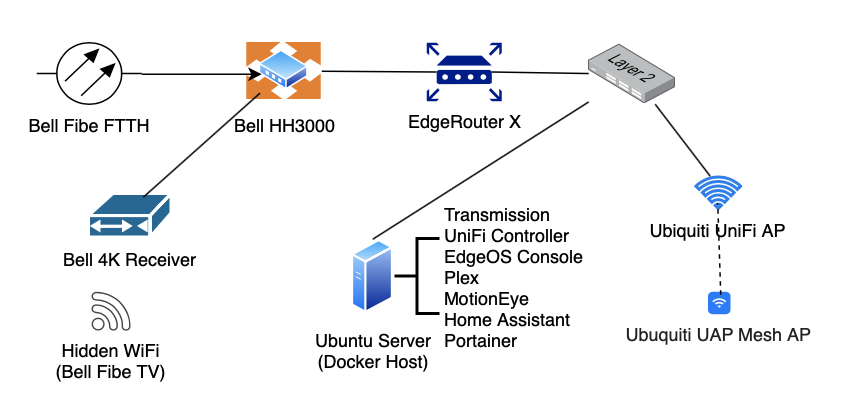
As a refresher, the HH3000 does not support bridged mode. Rather, it does offer a DMZ configuration. However, in my testing I have found the DMZ configuration to be unreliable. Generally, the HH3000 is not the among the best hardware out there. I have reduced the HH3000 to being simply a termination point for the Bell fiber connection. The WAN port of the EdgeRouter is connected to an ethernet port on the HH3000 and the EdgeRouter connects via PPPoE. I have seen some posts that suggest that VLAN tagging (VLAN 35) has to be enabled on the router that makes the call (the EdgeRouter X in my case) for PPPoE pass-through to work. However, this is not correct. VLAN tagging is not required. The VLAN tagging required for the Bell head is handled by the HH3000. The HH3000 supports PPPoE pass-through without any special configuration.
My network is segmented into separate IoT, Guest and Home networks. The IoT network hosts my smart devices such as Phillips Hue, Nest, various smart switches, voice assistants and cameras. Firewall rules on the EdgeRouter X isolate the IoT network from my Home network. However, hosts on the Home network can initiate connectivity to devices on the IoT network (i.e. IoT devices have no visibility to hosts on the Home network). The Guest network is setup in a similar manner, with similar firewall rules, except that bandwidth is limited to 50Mbps.
I have not moved my Apple TV devices to the IoT network. These devices remain on my Home network. During testing, I had lots of difficulty getting all Apple services (e.g. AirPlay, Apple remote from my iPhone, etc.) to work. My understanding is that the EdgeRouter and/or the UniFi must support multicast across subnets. However, I have been unable to get this working in way that all Apple services are available across subnets.
The Home network hosts all of the family smart phones, iPads, computers and related devices such as Apple watches. Some devices are hardwired via ethernet to the LAN ports on the EdgeRouter or to a TP-Link L3 switch. The network is logically separated via VLAN’s and therefore I need all of my network hardware to be Layer-3 aware.
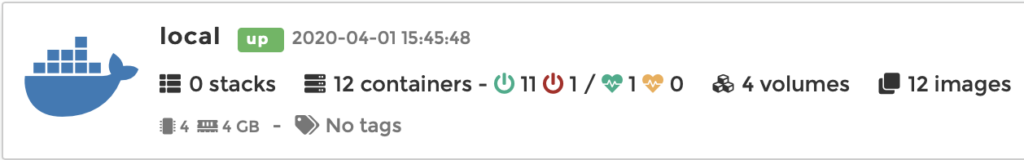
There is one physical computer that is hidden away in a closet that hosts my Docker containers:
DNS
Quad9 is not among the fastest available here in Toronto, Canada (cached response 0.014ms). OpenDNS still has the fastest response time. The reason may be due to infrastructure points-of-presence still being rolled out globally. I expect that the response times will improve over time. I have chosen OpenDNS as my primary DNS and Quad9 as secondary. My firewall rules force all DNS queries on the Guest and IoT networks to Google DNS (cached response 0.004ms). Although there is no advantage that I can think of for using different DNS on my Home and other networks, I just like the idea of them being separate 🙂
DHCP
DHCP services are defined for each network segment (Home, Guest & IoT). All DHCP servers are authoritative.
Firewall
The default action for packets entering the EdgeRouter X from the HH3000 is to drop the packet if the packet does not match any of the defined firewall rules. Packets with a state of ‘established’ or ‘related’ will be accepted. Thus, the only way a packet will be accepted is if the connection was initiated within the Home, Guest or IoT networks. Likewise, packets entering the home network from the IoT or guest networks will be dropped unless their state is ‘established’ or ‘related’. Hosts on the home network can initiate connections with hosts on the IoT network. Hosts on the IoT and Guest networks cannot establish connections to hosts on the Home network.
